172.16.252.214:4300 – Understanding the Address, Port and How It Works
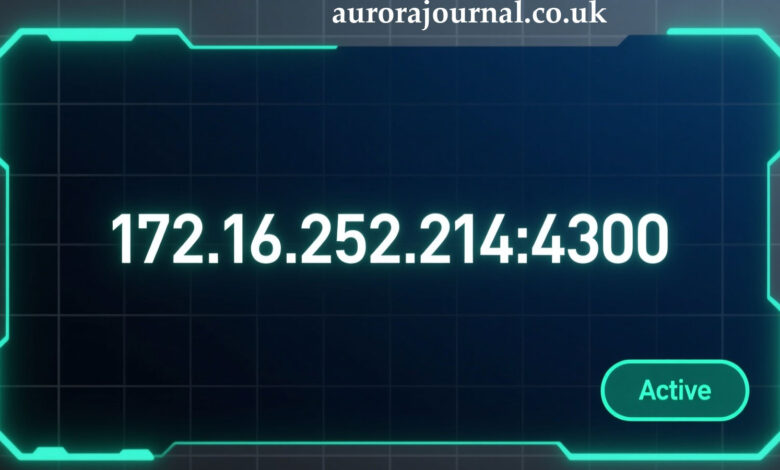
If you’ve encountered the notation 172.16.252.214:4300, it can raise questions: what does this address and port combination mean? How is it used in a network environment? And why might you be dealing with it? In this article, we’ll delve into the components of 172.16.252.214:4300, explore its role in network architecture, highlight typical use-cases, identify security implications, discuss troubleshooting steps, and answer common questions. By the end, you will have a clear understanding of how 172.16.252.214:4300 functions and how to work with it.
Decoding the Components: IP Address and Port
Let’s break down the notation 172.16.252.214:4300 into its two parts.
The IP address — 172.16.252.214
The segment 172.16.252.214:4300 is a private IPv4 address. It falls within the range 172.16.0.0 to 172.31.255.255 which is reserved for private network use (per RFC 1918). This means the address is not routable on the public internet—it is intended for internal network communication only.
This positioning implies the device assigned this address is likely part of a local area network (LAN) or similar private network segment.
The port number — :4300
The :4300 part is a TCP/IP port number. Ports act as endpoints for network services on a host; different services listen on different ports so that multiple services can operate concurrently on one IP. While ports like 80 (HTTP), 443 (HTTPS), 22 (SSH) are well-known, port 4300 is less standard and may be used by custom or less common applications or services.
Thus, when you see 172.16.252.214:4300, it essentially points to device 172.16.252.214 on port 4300 — i.e., “connect to this host, ask for service listening on port 4300”.
Putting it together
So the full notation addresses: “On internal network, reach host at private IP 172.16.252.214 and contact whatever service is listening on port 4300.” It might look like: http://172.16.252.214:4300/ or some other protocol if specified.
People Read Also : Exploring numberlina.com: Your Comprehensive Guide to the Platform
Why Use a Private IP + Custom Port Setup?
There are several reasons why a network administrator or internal system may be configured with a private IP and custom port such as 4300:
Internal service isolation
Using a private IP means the device is isolated from the public internet. It reduces exposure to external attacks and simplifies internal network management.
The custom port allows hosting of a service without interfering with more common ports. For example, an internal web application, database server, or management console might reside on port 4300 to avoid port conflicts or default port scrutiny.
Segmented network architecture
Many organisations separate internal services (e.g., development, management, monitoring) onto private IP spaces and custom ports. The combination of 172.16.252.214:4300 might serve a special role in such architecture—perhaps a monitoring dashboard, admin console, or internal API endpoint.
Security by obscurity (to some degree)
While not a strong security defence alone, using non-standard port numbers (like 4300) makes casual scanners and less-sophisticated attackers less likely to catch the service instantly. Combined with firewalls and proper access control, this helps.
Resource organisation
Network services inside a private network often use specific port assignments to segregate duties. The notation thus documents, “this specific host and port do this service”.
Potential Use-Cases for 172.16.252.214:4300
Here are illustrative scenarios where 172.16.252.214:4300 might be used.
Internal Web or API Service
Imagine a company hosts an internal dashboard accessible only to employees on the LAN. The server might be at 172.16.252.214 and for whatever reason the dashboard listens on port 4300 (rather than the usual port 80/443). Users would navigate to http://172.16.252.214:4300/ to reach it.
Database or Backend Service
A backend service (e.g., a microservice, internal API) might run at 172.16.252.214 on port 4300 and be accessed by other services or internal clients. By choosing port 4300, the team avoids interfering with standard ports and keeps the service clearly identified.
Monitoring / Management Console
An appliance or tool within the private network might host a management UI at 172.16.252.214:4300, accessible only from the LAN or via VPN. This helps separate admin access from public facing equipment.
Security Considerations
Whenever you have a host-port endpoint such as 172.16.252.214:4300, there are several security angles to keep in mind.
Access control & firewalling
Ensure that only authorised IPs or sub-networks can reach 172.16.252.214:4300. A firewall (hardware or software) should restrict inbound connections and limit exposure.
If the service is reachable via VPN only, that’s better design than exposing it openly.
Service hardening
The service listening on port 4300 should be up-to-date with patches, less-privileged if possible, and have strong authentication if applicable. Avoid running unnecessary features or default credentials.
Network segmentation
The host 172.16.252.214 should ideally sit in a VLAN or network segment with appropriate restrictions—separate from general-purpose user devices—to limit lateral movement if the host gets compromised.
Logging and monitoring
Monitor traffic to port 4300 for anomalies. Failed login attempts, unusual access patterns, high data transfer should raise flags. Keeping logs helps for forensic or operational review.
Avoid mis‐documentation
Make sure that 172.16.252.214:4300 is clearly documented (internally). Non-standard ports sometimes get forgotten and pose an unwanted security risk if accidentally exposed.
Troubleshooting 172.16.252.214:4300
When connecting to 172.16.252.214:4300, or setting up that endpoint, you may run into issues. Here are common ones and how to address them:
1. Connection refused or time-out
-
If a client tries to reach 172.16.252.214:4300 and gets “connection refused”, likely no service is listening on port 4300 on that host. Verify the service is running and bound to that port.
-
If time-out, maybe a firewall blocks access or the host is offline/unreachable.
2. Incorrect service binding
Check that the service is configured to listen on the correct IP (172.16.252.214) and port (4300). Sometimes service configs default to localhost or incorrect interface.
3. Firewall/Network blocking
Inside the LAN or across VLANs, the path to 172.16.252.214:4300 may be blocked. Use ping/traceroute, then attempt netcat/telnet to port 4300 to test connectivity. Ensure the firewall rules permit traffic.
4. DNS / Hostname confusion
If users use a hostname (e.g., mydashboard.internal) that resolves to 172.16.252.214, confirm DNS is correct. If they use the raw IP plus port, still check routing.
5. Service certificate / encryption issues
If the service on port 4300 uses HTTPS/SSL, certificates may need proper names, etc. Browser may warn if invalid cert for IP vs hostname. For internal services sometimes self-signed certs are used—be mindful of trust and user training.
6. Performance / Latency
If 172.16.252.214:4300 is reachable but slow, check latency, bandwidth, host load, whether port 4300 service is hogging resources or poorly configured. Use logs, resource monitoring on the host.
Best Practices for Deploying Endpoints like 172.16.252.214:4300
When you are designing or auditing a system where a designation like 172.16.252.214:4300 is used, keep these best practices in mind:
-
Use meaningful port numbers (document what port 4300 is for) and consistent conventions.
-
Use internal DNS or aliasing so users or services don’t remember raw IP:port always. e.g., dashboard.mycompany.local -> 172.16.252.214:4300
-
Limit access via network controls (firewall, ACLs) and authentication.
-
Monitor and log accesses to that port; set alerts for anomalies.
-
Keep internal services on private IP space (like 172.16.x.x) so they are not exposed inadvertently.
-
Regularly review which services listen on custom ports and disable unused ones.
-
If the service must be accessible externally (via VPN or proxy), use secure tunnelling rather than exposing 172.16.252.214:4300 directly to the internet.
-
Name your hosts clearly (e.g., host-172-16-252-214) or use descriptive DNS names rather than remembering raw IP.
Conclusion
The address and port notation 172.16.252.214:4300 is a simple yet powerful representation of a network service endpoint: a host at private IP 172.16.252.214 listening on port 4300. While such combinations are common in internal networks and custom services, they carry responsibilities: proper configuration, security controls, documentation, monitoring and maintenance.
Frequently Asked Questions (FAQs)
Q1: What exactly is 172.16.252.214:4300?
It is the notation combining IP address 172.16.252.214 (a private IPv4 address) and port 4300. It means a network service is accessible on host 172.16.252.214 listening on TCP (or UDP) port 4300.
Q2: Can 172.16.252.214:4300 be reached from the internet?
Normally, no — because 172.16.252.214 is in a private address range (172.16.0.0/12) and is not publicly routable. Unless NAT or some routing is done to expose it, only devices on the same private network or via VPN/bridge can access it.
Q3: Why the port number 4300 — is that standard for something?
Port 4300 is not one of the well-known “standard ports” (like 80 or 443). It is likely used for a custom service or internal application. The choice depends on the organisation’s network design.
Q4: What if when I try to connect to 172.16.252.214:4300 I get “connection refused”?
This usually means the IP is reachable but no service is listening on port 4300 on that host. You should check if the service is running, bound to that port, and that firewall rules are not blocking it.
Q5: Could this be a security risk?
Yes, if mis-configured or exposed insecurely. Even though 172.16.252.214 is private, if the network is breached or if port 4300 is exposed unintentionally (for example via port forwarding), then an attacker could access the service. Use proper segmentation, authentication, and patching.
Q6: How do I know what service is running on 172.16.252.214:4300?
You can attempt to connect (e.g., via browser if it’s HTTP, or via telnet/netcat to test TCP). You can also check the host itself: list listening ports (e.g., using netstat -tulpn on Linux) and see what process is bound to port 4300. Internally, the network documentation should indicate which service uses that host/port.
Q7: Are there any special configuration tips for port 4300?
Yes — treat it like any other service port: ensure only necessary access, apply encryption/auth, log access, and monitor for abnormal behaviour. If it’s web-based, secure it with HTTPS and prefer hostnames over raw IPs.
Q8: Could I change the port from 4300 to something else?
Yes. If you control the service and configuration, you can assign any unused port (within range) for the service. Just ensure that all clients know the new port and network/firewall rules are updated accordingly.



